Webhooks
AdminUI contains three webhooks to extend AdminUI functionality and integrate it with your IdentityServer and custom Identity needs. These webhooks hold no functionality themselves but call secured endpoints to trigger outside functionality, this could within your IdentityServer instance or a separate API.
Password reset webhook- This webhook allows AdminUI to trigger custom password reset logic contained elsewhere.User registration webhook- This webhook will trigger any additional account setup process your security solution might have.Reset mfa webhook- This webhook will trigger custom logic used to reset a user's Multi-Factor Authentication.Delete session webhook- This webhook will trigger when you press the delete button on a session in a session management table
Webhook Configuration Page
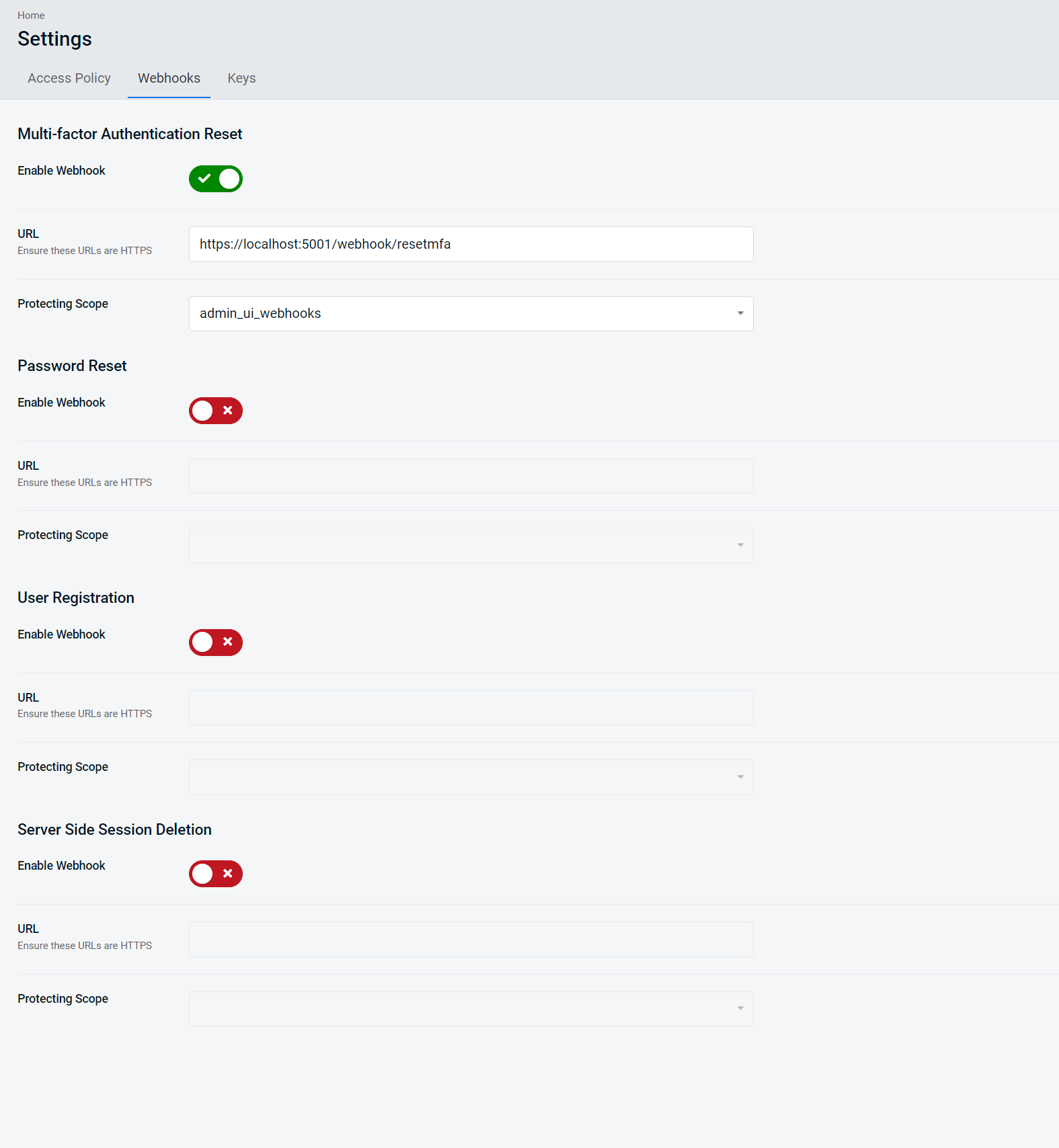
As of AdminUI 5.6, you can manage your webhook configuration within AdminUI. You can manage webhook configuration by navigating to the Webhooks tab in the Settings area of AdminUI.
Here you can enable/disable the three webhooks, set the endpoint URLs, and choose the desired protecting scope.
Triggering Password Reset and Reset MFA
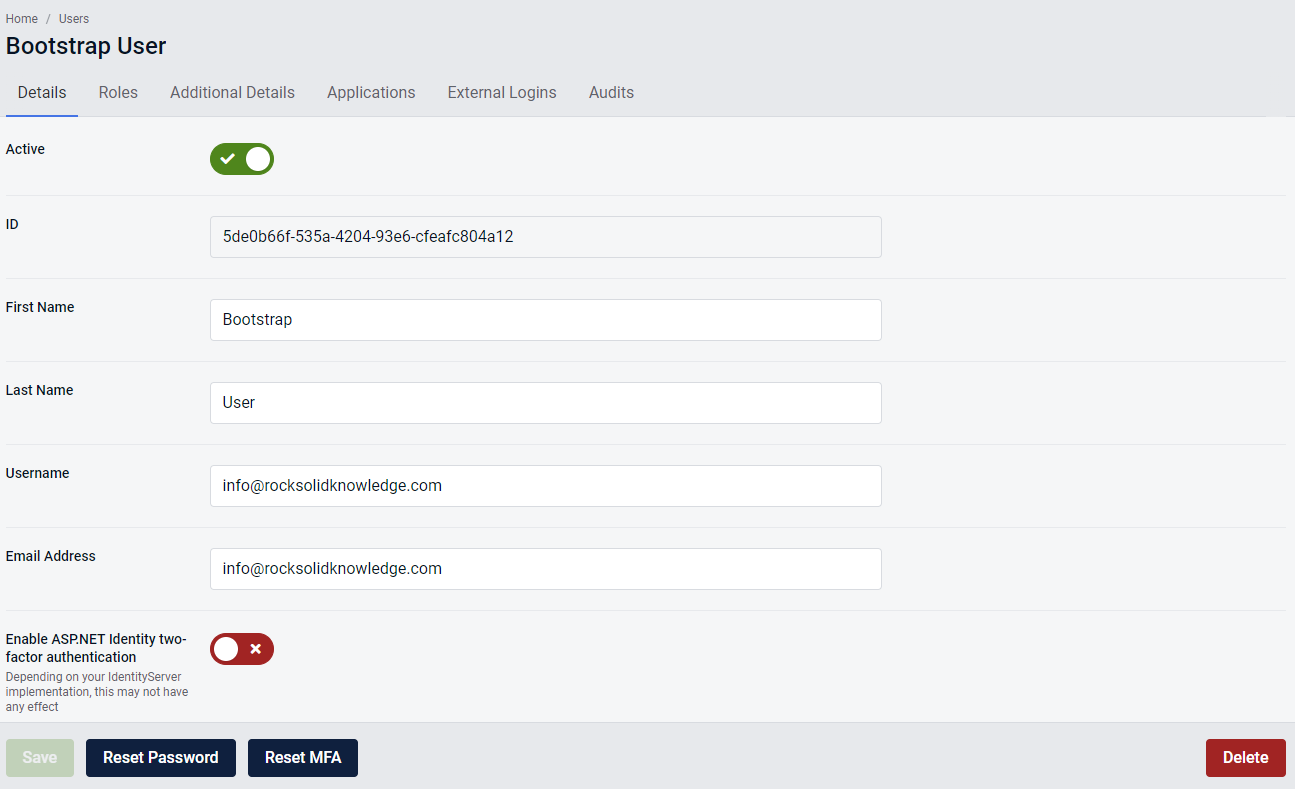
After navigating to a user details page, you will find the two buttons used to trigger either the Password Reset webhook or the Reset MFA webhook. If enabled in the Webhook Configuration page, clicking on the desired button will trigger the webhook.
If the webhook has not been enabled in the Webhook Configuration page, clicking on the webhook button will direct you to documentation that will inform you on how to configure the webhook.
Triggering User Registration Webhook
If account creation succeeds and the User registration webhook has been enabled, then the webhook will trigger. If the user registration webhook has not been enabled user registration will still complete successfully, however the webhook will not be called.
The recommended way to use this webhook is to send an email to the user with a link to activate their account and set their initial password.
Triggering the Delete Session Webhook
If setup this webhook fire when you click the red x on a record in a session management table. Information about this feature can be found earlier in the documentation
This webhook will send an HTTP Delete to the url of your choosing, including the Session ID in the path. E.g:
https://localhost:5003/4b3c19ac-cce4-47c5-ac0e-eb79da45944b
For an example of how to implement this webhook with the default Duende session management implementation see our sample
Authorization
The webhooks will need to be to secured by your IdentityServer. You can choose a scope per endpoint in the Webhook Configuration page.
To ensure your webhooks are secured against public use, they should check for a bearer token, issued by your IdentityServer installation, that contains this scope.
The configuration of a webhook endpoint is detailed in the Webhook Endpoint Configuration page
Client
As of AdminUI 5.6, webhook client creation/deletion is handled for you by AdminUI. On enabling your first webhook, AdminUI will inform you that a client is about to be created. The client will try and use the ClientId and ClientSecret fields within your API configuration.
If AdminUI cannot find any values for ClientId or ClientSecret configuration fields, it will use a default clientId (admin_ui_webhooks) and a default client secret. You can view the secret's unhashed plaintext value in the ConfigurationEntries table under the webhooks key.
The client also uses the client_credentials grant type.
Webhook Configuration Migration
If you are upgrading AdminUI to a version above 5.6 and you are using webhooks, your webhook configuration will be migrated from your API configuration to the ConfigurationEntries table in your IdentityServer. This will happen during the first run of the API.
If you have any values against the webhook URL's in your API config or if you have both a ClientId and ClientSecret, AdminUI will create a client for you to use as a webhook client. The client will use the default admin_ui_webhooks protecting scope.